Our Approach
We take a structured, phased approach to modernizing and securing your IAM environment. Our consultants work alongside your technical and governance teams to ensure every step delivers measurable outcomes.
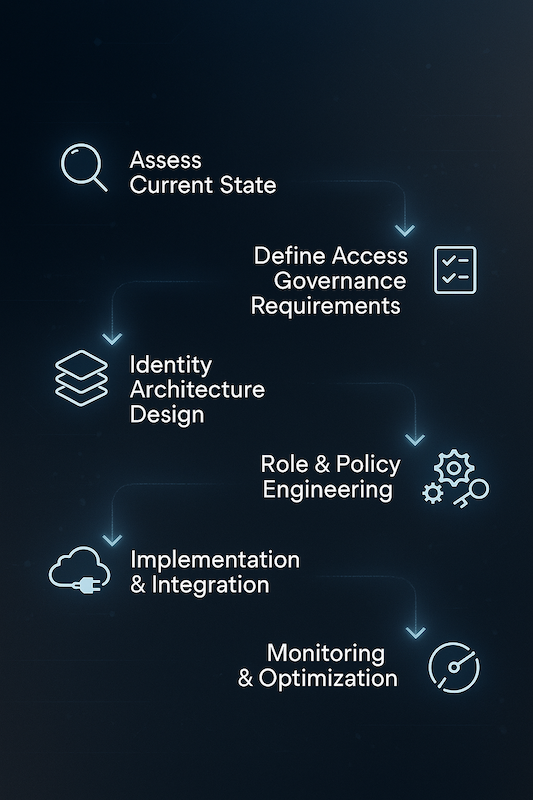
Phase 1: Assessment & Current-State Review
We take a structured, phased approach to modernizing and securing your IAM environment. Our consultants work alongside your technical and governance teams to ensure every step delivers measurable outcomes.
Phase 2: Define Access Governance Requirements
We collaborate with stakeholders to define governance policies aligned with business objectives, compliance obligations, and operational needs. This includes access review requirements, segregation of duties, approval workflows, and accountability models.
Phase 3: Identity Architecture Design
We design a scalable IAM architecture that fits your hybrid or cloud-native environment. This may include central identity providers (IdPs), federated authentication, SSO integration, multi-factor authentication (MFA), and directory service optimization.
Phase 4: Role & Policy Engineering
We develop logical role models (RBAC or ABAC), group structures, and access policies to enforce least privilege and streamline administration. Our approach ensures roles are manageable, auditable, and aligned to business functions.
Phase 5. Implementation & Integration
We support the rollout and integration of IAM technologies such as Azure AD, Okta, Ping Identity, or open-source platforms. This includes automation of provisioning, SSO/MFA configuration, and enforcement of access policies.
Phase 6. Monitoring & Optimization
We implement processes and tooling to continuously monitor access activity, detect anomalies, and automate periodic access reviews. As your environment evolves, we help you optimize policies and stay ahead of risk and compliance challenges.
