A Practical, Phased Path to Zero Trust Adoption
Our Approach
We take a phased, business-aligned approach to Zero Trust focusing on practical outcomes that reduce risk and improve control without unnecessary complexity.
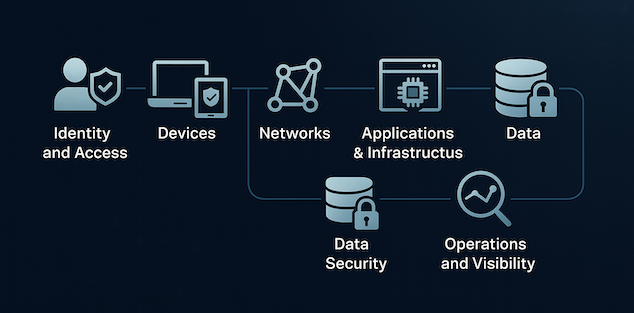
Our strategy balances security goals with operational realities, ensuring alignment with your existing infrastructure, compliance obligations, and growth plans. From initial assessment to full-scale implementation, we help you build a scalable Zero Trust model that fits your environment and delivers measurable value.
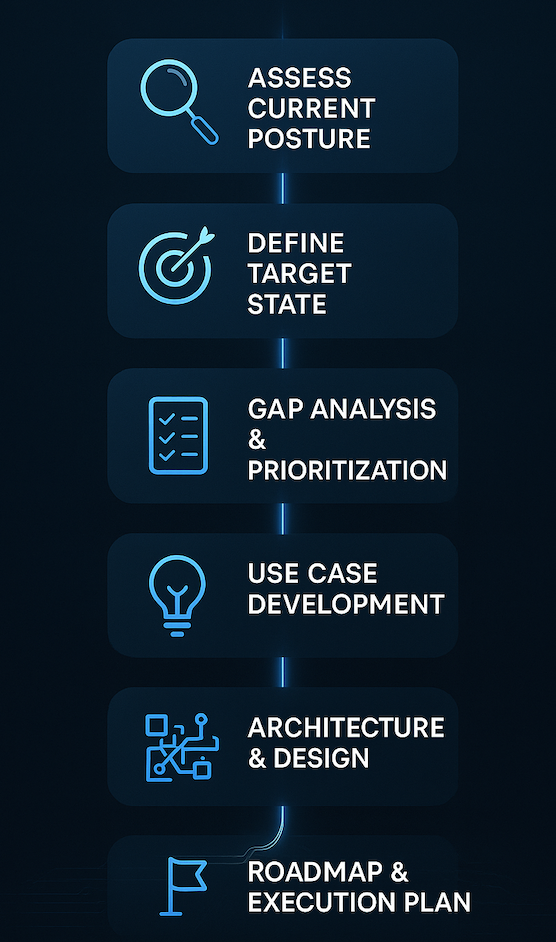
1. Assess Current Posture
Before implementing Zero Trust, we conduct a comprehensive security posture assessment.
- Identify vulnerabilities, misconfigurations, and high-risk gaps.
- Map the current threat landscape facing your organization.
- Evaluate identity assurance, device compliance, data flows, and access models.
- Use a hybrid maturity model (GSA, NIST SP 800-207, CISA ZTMM) as a scoring lens.
This step builds the foundation for Zero Trust by showing where you stand today.
2. Define Target State
We establish a Zero Trust vision statement that aligns to your business goals, risk tolerance, and regulatory requirements.
- Define policy enforcement points (PEPs) and policy decision points (PDPs) across identity, workloads, and data.
- Ensure inclusion of device identity, user access validation, and data classification policies.
- Bake in continuous monitoring, MFA, encryption, and secure communication channels.
This step ensures you have a clear, business-aligned end state to work toward.
3. Gap Analysis & Prioritization
With your posture assessed and target defined, we identify the gaps that matter most.
- Highlight risks tied to identity, device trust, workload segmentation, and data security.
- Recommend mitigation actions such as implementing access controls, enabling conditional policies, and scheduling vulnerability scans/pen testing.
- Prioritize initiatives by impact on business risk, compliance urgency, and complexity of rollout.
This phase creates a risk-driven sequence of Zero Trust milestones.
4. Use Case Development
We create high-value Zero Trust use cases that balance quick wins with strategic outcomes.
- Secure remote access with posture validation and MFA.
- Privileged access enforcement with just-in-time (JIT) and just-enough-access (JEA).
- Device identity enforcement to ensure only trusted endpoints access critical resources.
- Data-centric security policies (classification, encryption, contextual controls).
Each use case demonstrates tangible business value while reinforcing your Zero Trust foundation.
5. Architecture & Design
We translate Zero Trust principles into a practical, tool-agnostic architecture.
- Map all devices, networks, applications, and data flows — know your architecture inside and out.
- Define trust zones, microperimeters, and segmentation gateways.
- Integrate identity providers, monitoring platforms, and secure communication channels (MFA, TLS, encryption).
- Ensure visibility and telemetry across all environments.
This step delivers a Zero Trust reference design that fits your business and tech stack.
6. Roadmap & Execution Plan
Finally, we deliver a phased roadmap for Zero Trust implementation.
- Define milestones aligned with CISA’s maturity levels (initial, advanced, optimized).
- Assign ownership (security, IT ops, governance).
- Incorporate change management, secure adoption practices, and continuous improvement cycles.
- Include metrics and KPIs (e.g., % of assets behind ZT policy, MTTD/MTTR, % of privileged accounts with JIT).
This ensures Zero Trust is sustained, measurable, and continuously improved over time.